Chip!
In modern engineering organizations, effective monitoring requires minimizing alert noise and reducing setup complexity. Chip, developed by former Netflix engineers, addresses these challenges by automatically analyzing telemetry data—including custom metrics—to surface critical issues without extensive configuration. Its built-in support for OpenTelemetry allows quick integration into existing systems, typically within 30 minutes. Chip helps engineering teams maintain focus on core development tasks while ensuring reliable system observability.
AWS CloudWatch Metrics
AWS CloudWatch provides real-time monitoring of your AWS resources and applications by collecting key metrics and logs. Integrating CloudWatch metrics with Cardinal’s Chip via AWS Firehose is quick and straightforward, taking just a few minutes to set up. Once integrated, Chip analyzes your CloudWatch metrics alongside other telemetry data, such as Kubernetes metrics and logs, delivering comprehensive insights into your system’s performance without the hassle of manually managing CloudWatch alerts and alarms.
Prerequisites
- A Cardinal Gateway Collector installed in a Kubernetes cluster.
- AWS permissions to create a Data Firehose stream and a CloudWatch metric stream, s3 buckets, and the associated IAM roles and policies.
- Permission in the Kubernetes cluster to create an Ingress resource with TLS termination.
Quick Start
Configure Cardinal Gateway Collector
- Log into your account at CardinalHQ (opens in a new tab).
- Navigate to the Pipelines configuration tab.

- Select your Gateway collector from the dropdown.
- Click Add a source (bottom-left of the pipeline graph).
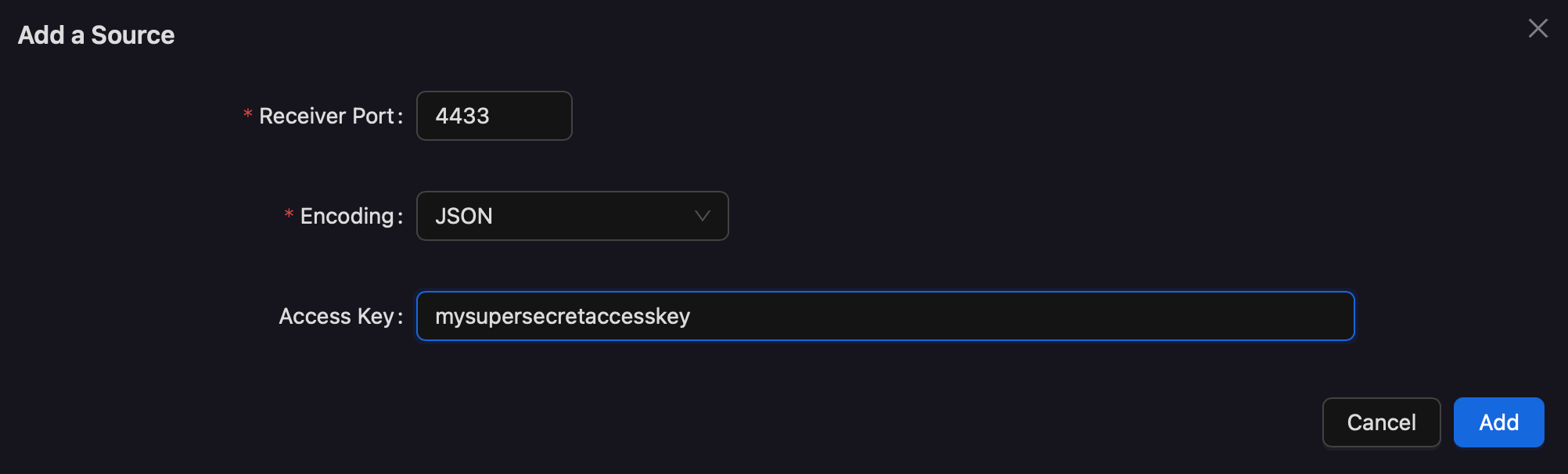
- Choose AWS Firehose Metrics.
- Set a port between
1024and65535. The acutal port here does not matter, and will be used by the ingress step to route traffic to the collector. The port should not already be used by another receiver on this collector. - Choose
JSONas the encoding. - Create and securely store an Access Key for authentication. This access key is
used to authenticate the AWS Firehose stream to the Cardinal Gateway collector.
Its value should be a random string of at least 16 characters.
Configure Kubernetes Ingress
- AWS Firehose requires a TLS-secured (
https://) endpoint. - Set up Kubernetes Ingress with a TLS certificate. Refer to your environment’s specific documentation to accomplish this step.
Configure AWS Firehose
- Log into the AWS Console.
- Navigate to Amazon Data Firehose.
- Click Create Firehose Stream.
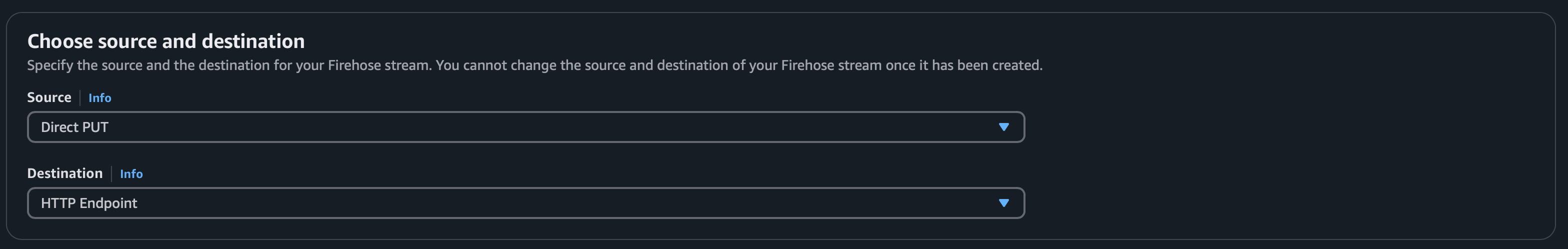
- Source: Select Direct PUT.
- Destination: Select HTTP Endpoint.
- Enter your TLS-secured collector endpoint (
https://...).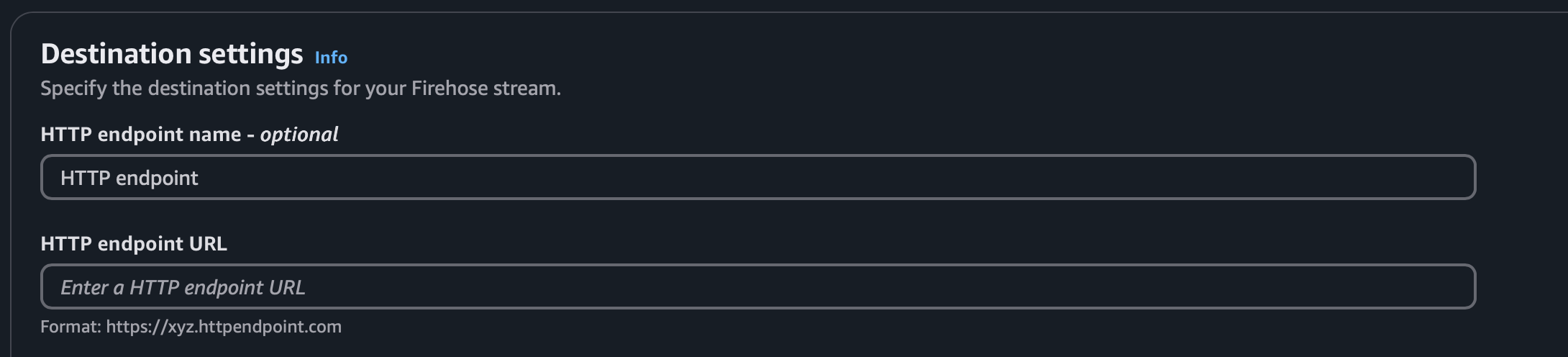
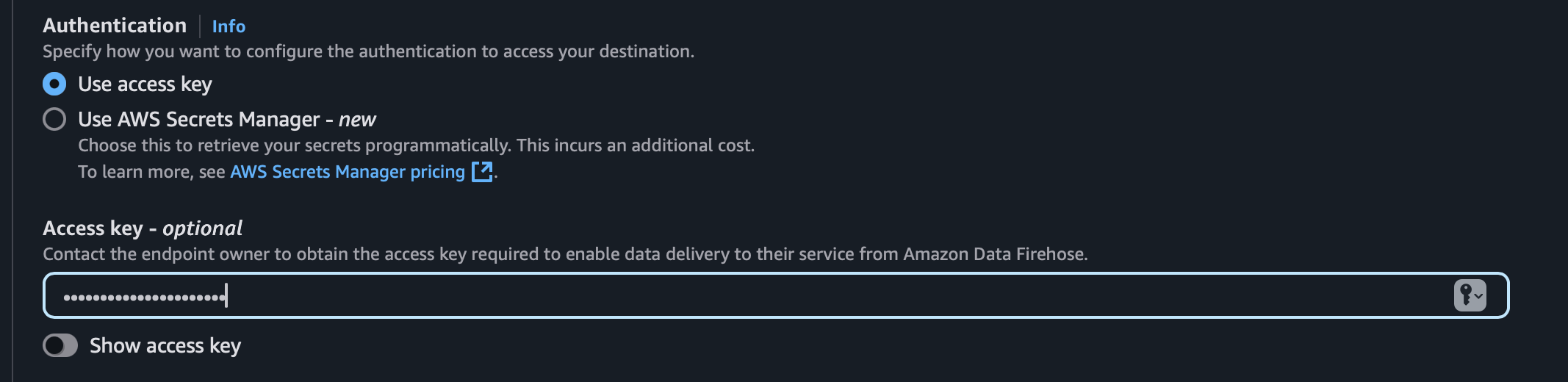
- Authentication: Select Use access key and input your earlier-created key.
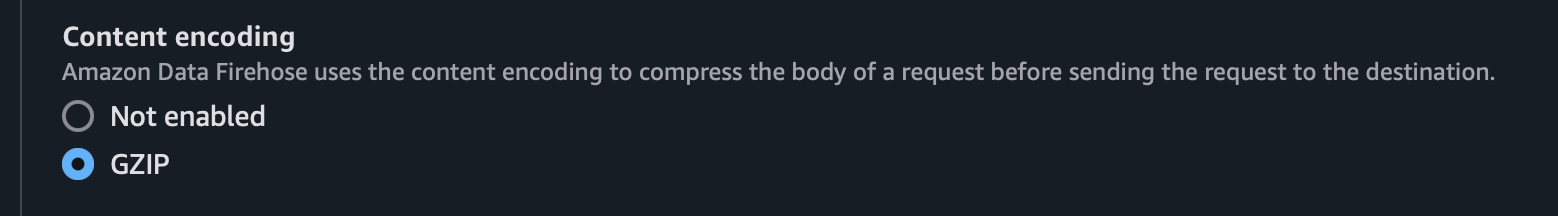
- Content Encoding: Select GZIP.
- Optional: Add additional OpenTelemetry attributes via Add parameter.
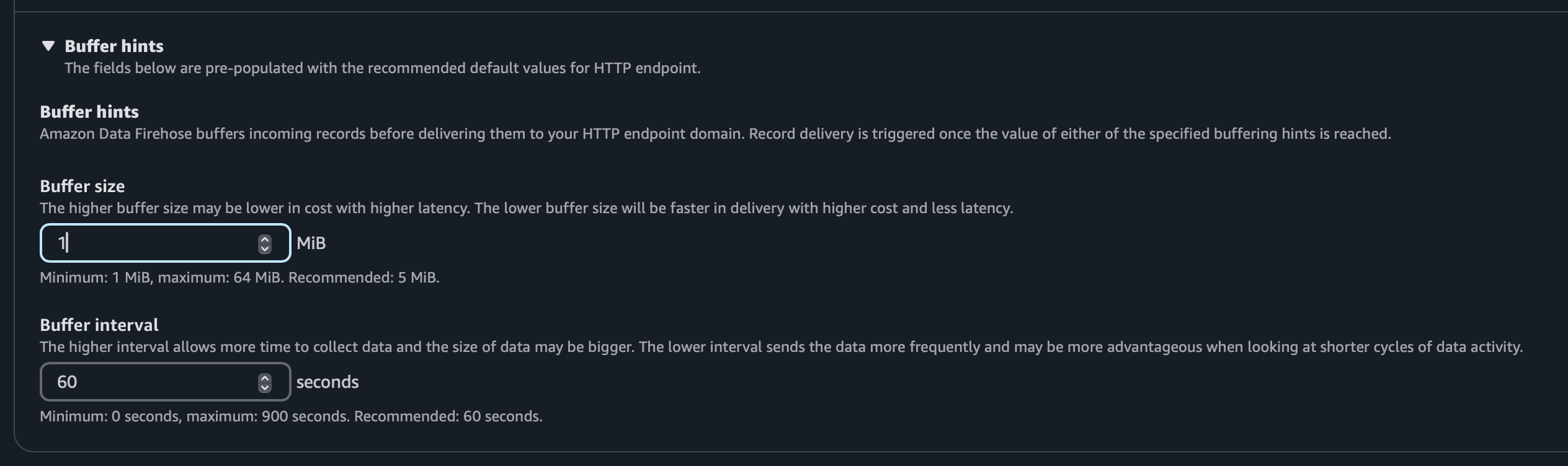
- Expand Buffer hints, and set "size" to "1" and "interval" to "60".
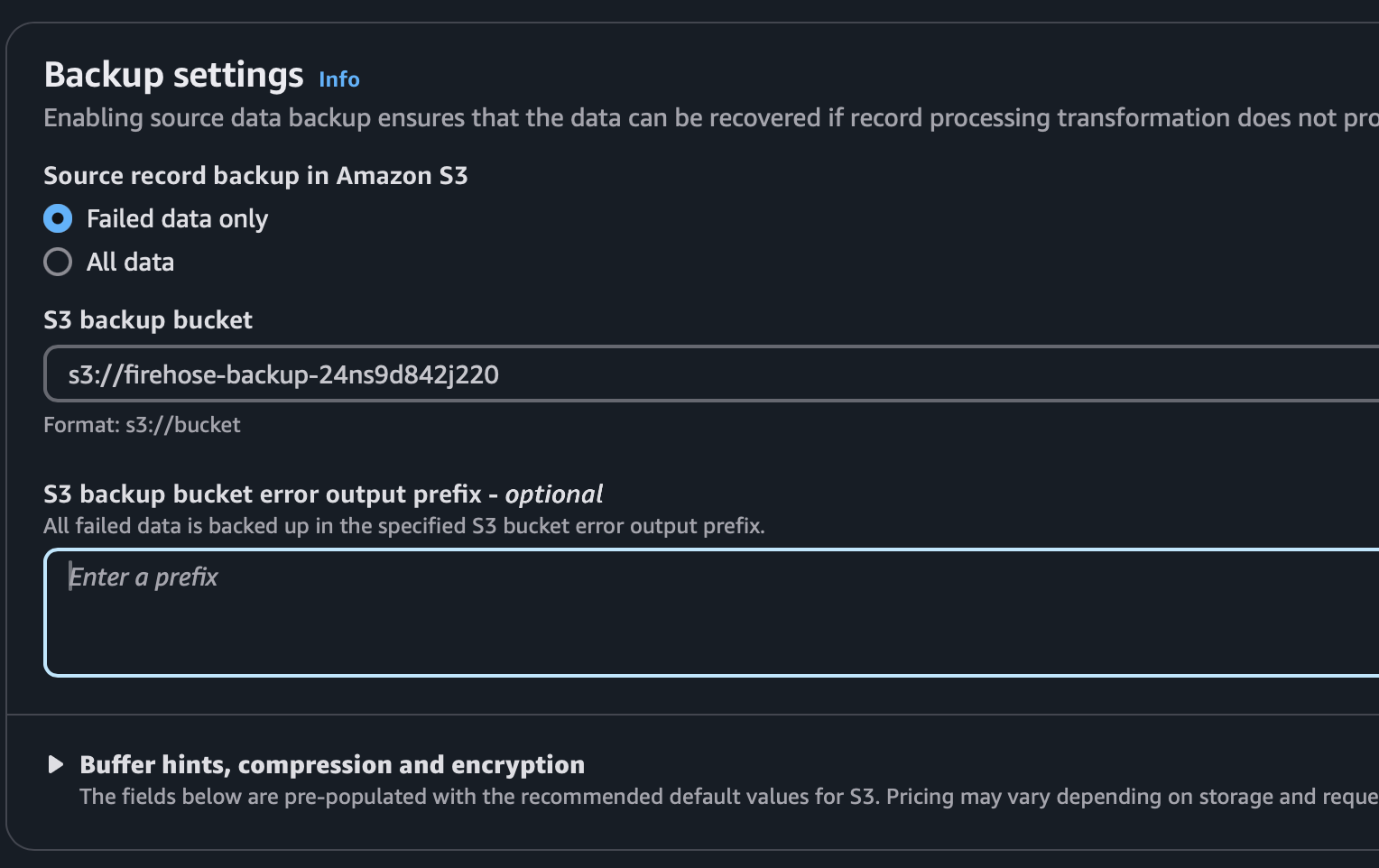
- Choose S3 Bucket options:
- Recommended: Select Failed data only.
- Set retention policies and encryption as required for compliance.
- Click Create firehose stream.
Configure AWS CloudWatch Stream
- In AWS Console, navigate to CloudWatch → Metrics → Streams.
- Click Create metric stream.
- Select Custom setup with Firehose.
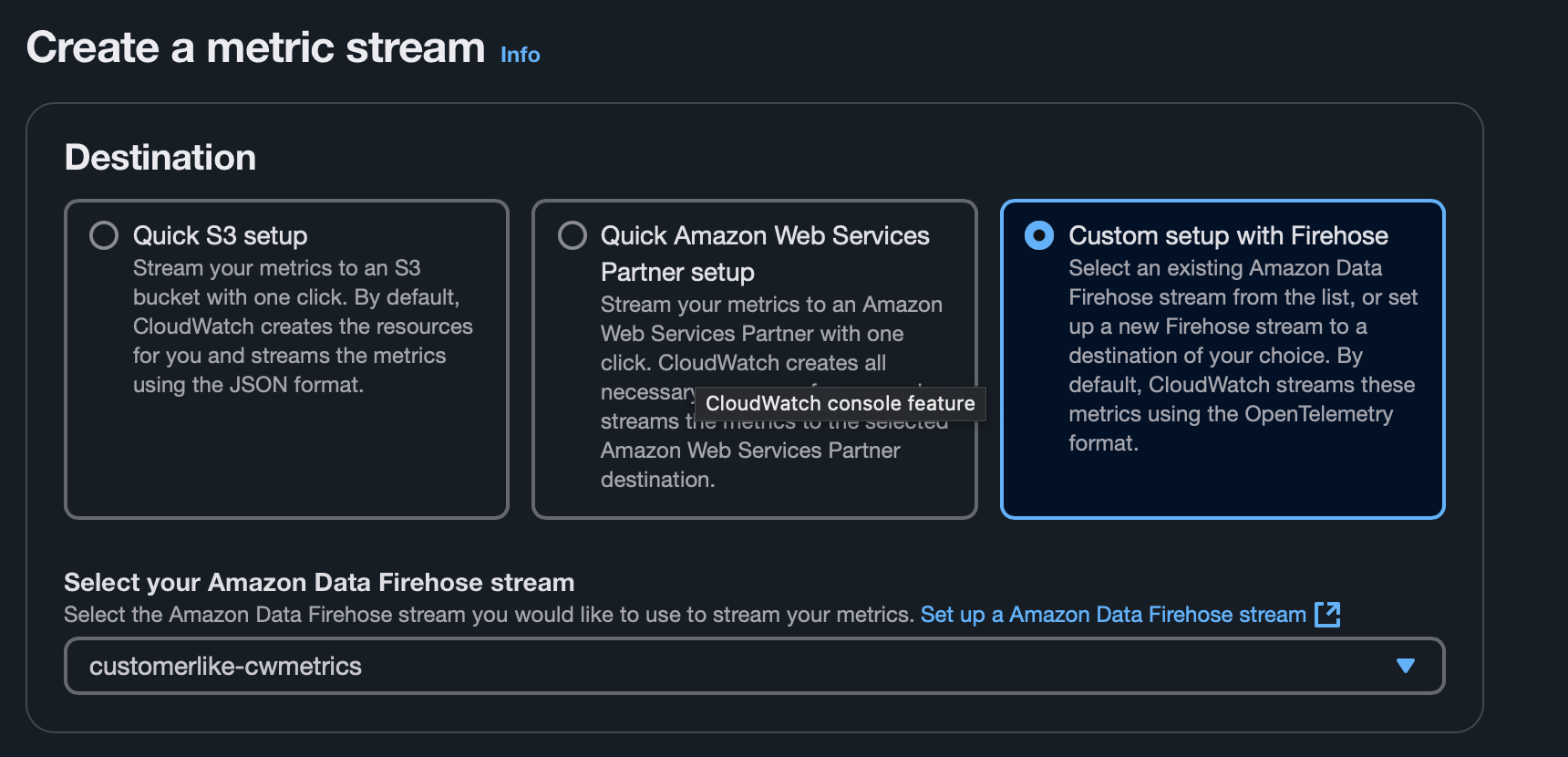
- Select your newly created Firehose from the dropdown.
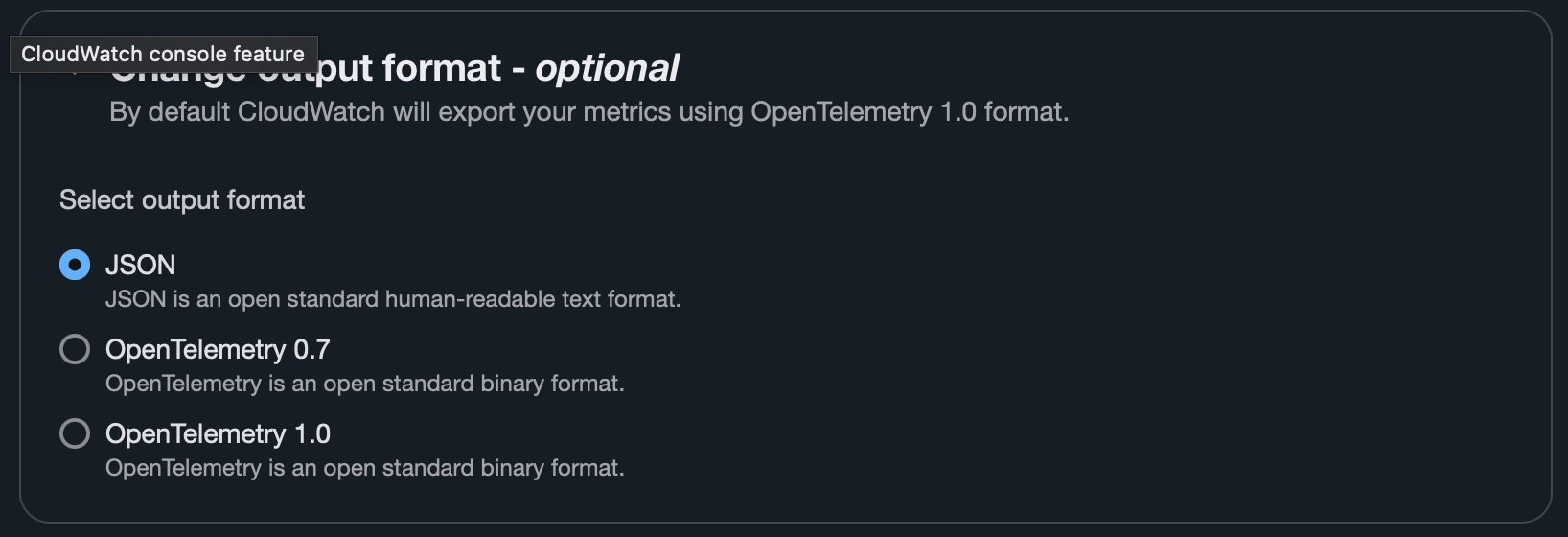
- Change output format to JSON.
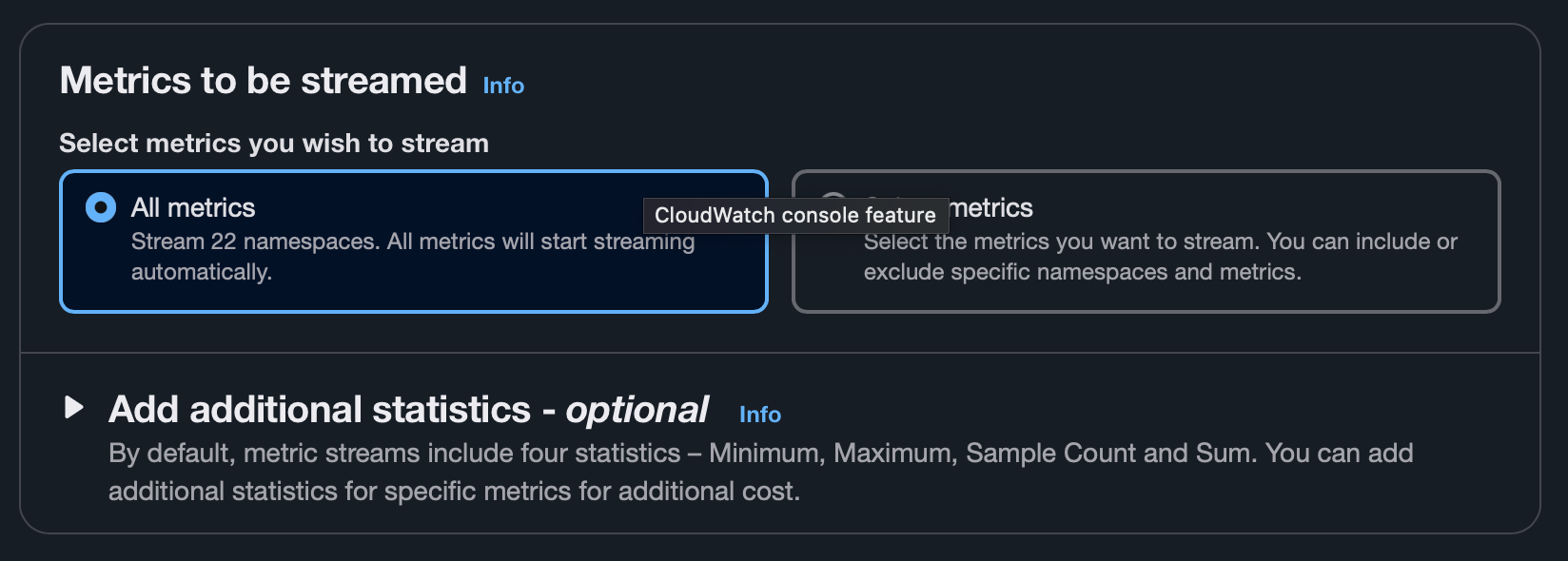
- Select desired metrics (all or specific services, e.g., RDS). This list can be changed later.
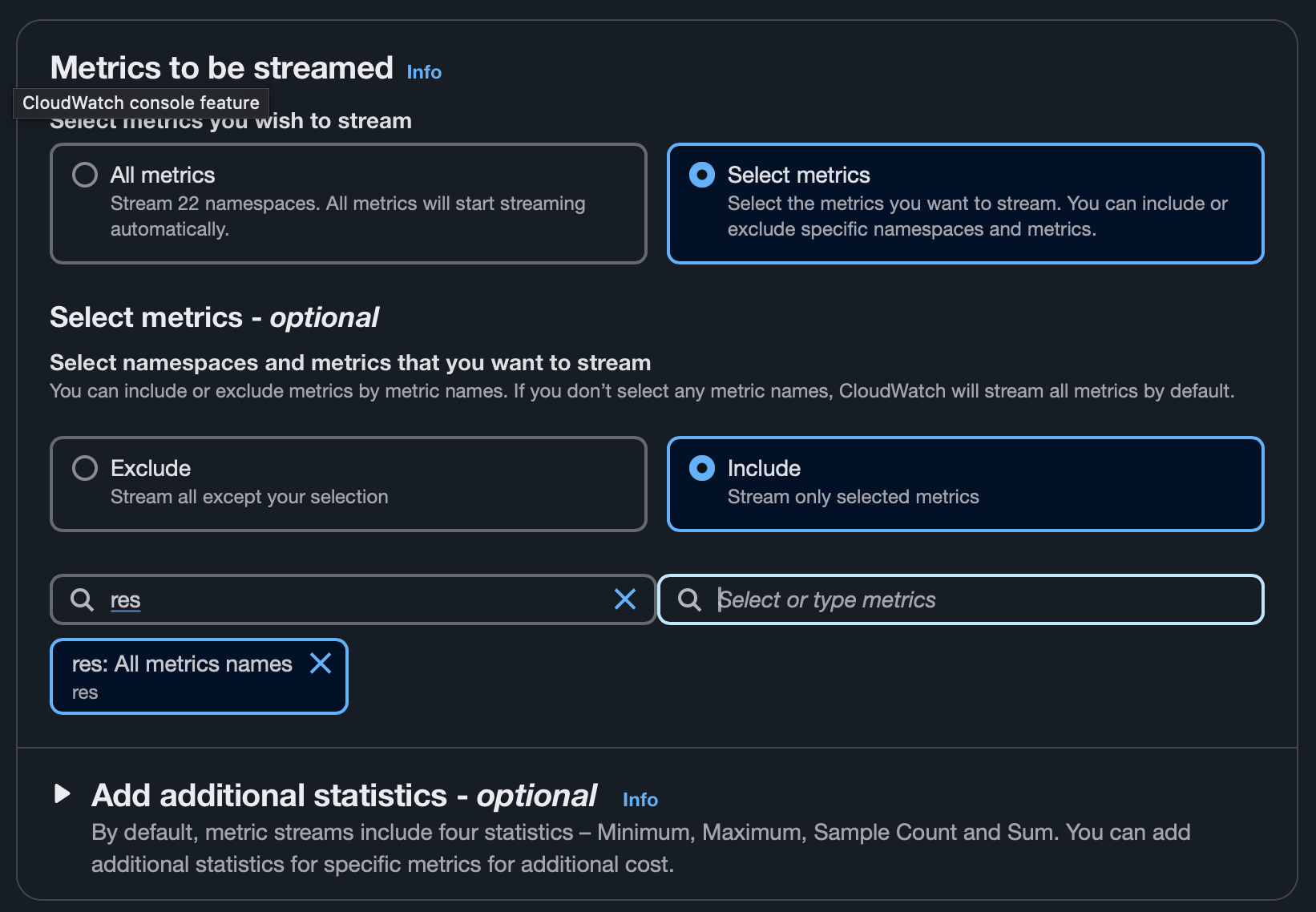
- Name your metric stream (optional).
- Select Custom setup with Firehose.
- Click Create metric stream.
Verify that metrics are flowing
- Navigate back to the Data Firehose service, and examine the metrics for the firehose you created.
- After some short time, you should see data coming in, and data being sent over HTTP. There should be no errors logged.
- If you see errors, check
- That the ingress into your collector is fully set up and functional
- That the endpoint configured on the firehose is correct.
- If you see no data
- Check that the CloudWatch metric stream is sending data to the Firehose.
Relax
Chip is now actively monitoring your AWS CloudWatch metrics. You can relax as Chip proactively identifies anomalies and correlates metric data with your Kubernetes infrastructure.